
Description
Check if your Linux computer or phone is secure using TPM2 and cryptography. It generates private keys tied to the device's state for trustworthy signatures. Verify identities and key possession—though phone security depends on the OS. Tools like cryptographic-id-rs and Auditor (GrapheneOS) assist with attestation.
Screenshots
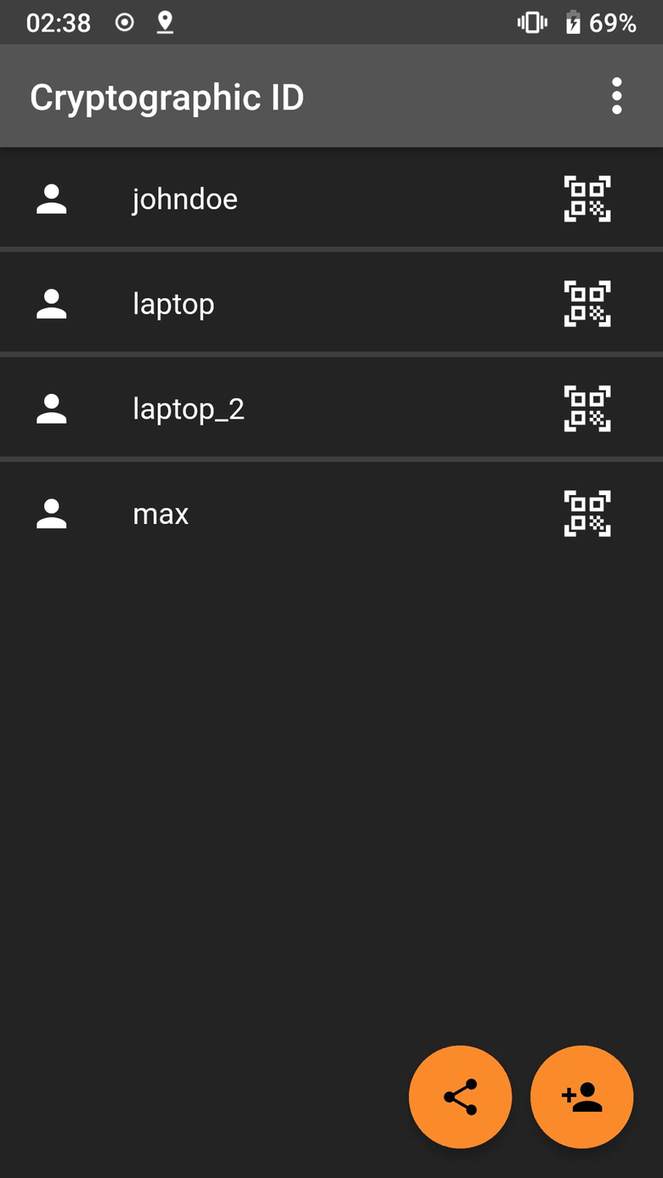
Click to view full size
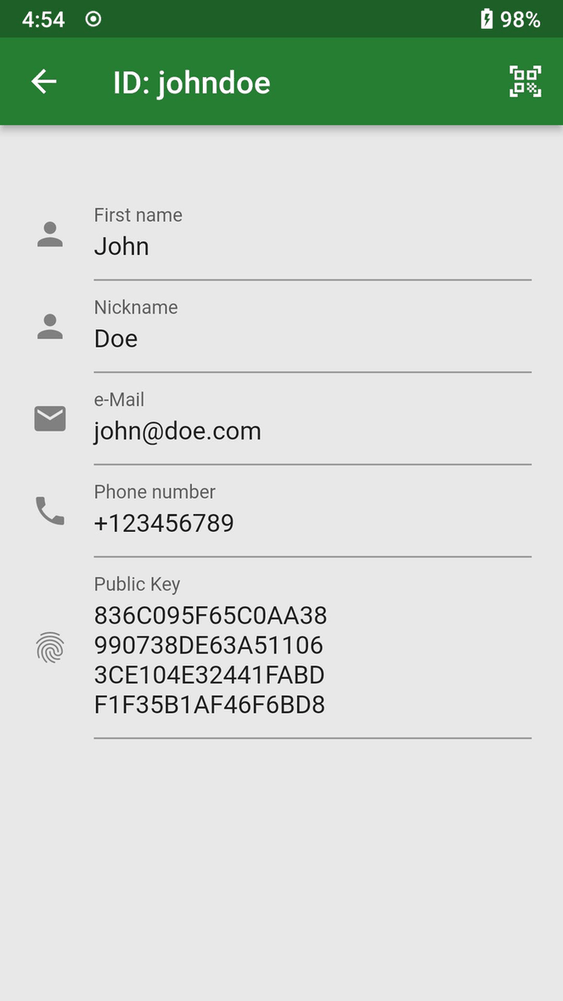
Click to view full size
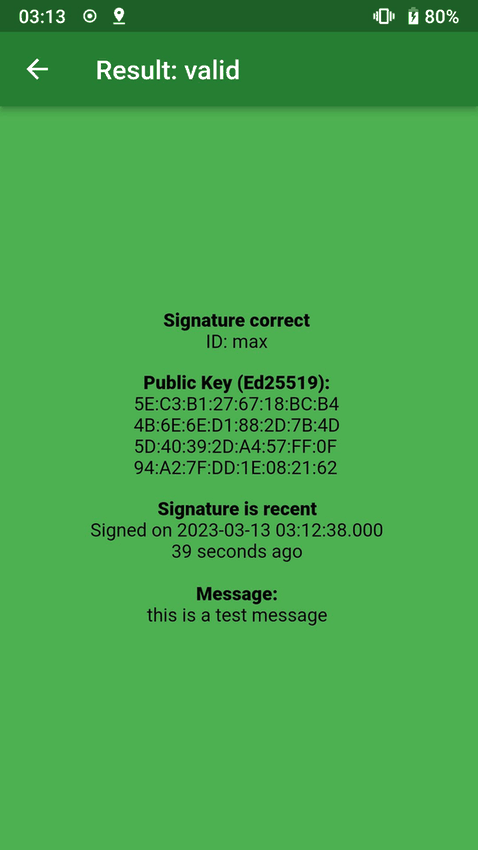
Click to view full size
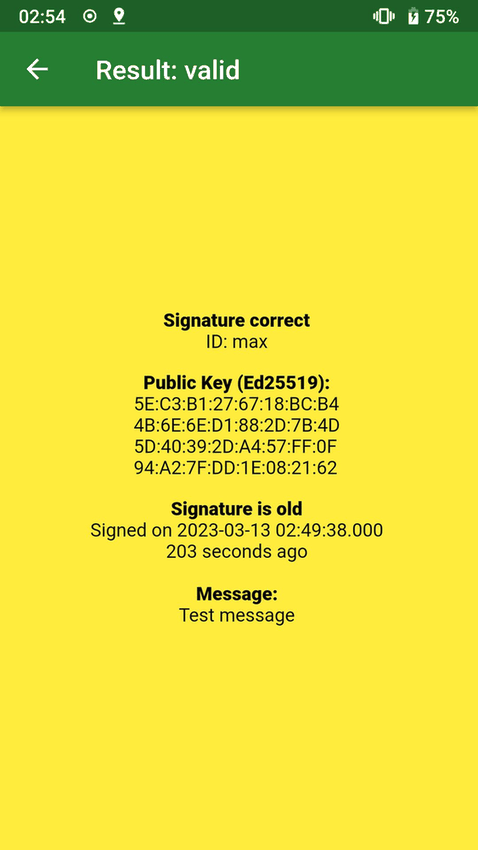
Click to view full size
Click to view full size
Click to view full size
